New tests have revealed that hardware wallets are vulnerable, with possibility of PINs getting revealed.
The test revealed that two new popular hardware wallets could have been hacked only by a resourceful and a well sophisticated attacker.
But hardware wallets are the supermax of Bitcoin security, they are still the safest place to store Bitcoin or any other cryptocurrency. So, why are these wallets witnessing brute force in recent times?
Coindesk in an article said that Customers of Ledger were being attacked through a phishing email with cloned features from Ledger.
A Reddit user notified the r/ethfinance group of the email which looked so real and had the professional touch that recipients of the email could be tricked to follow its directives.
The email tried to portray a wide scale attack on all ledger wallets and left a clickable link at the base to redirect users to another webpage.
Here’s what the email says…
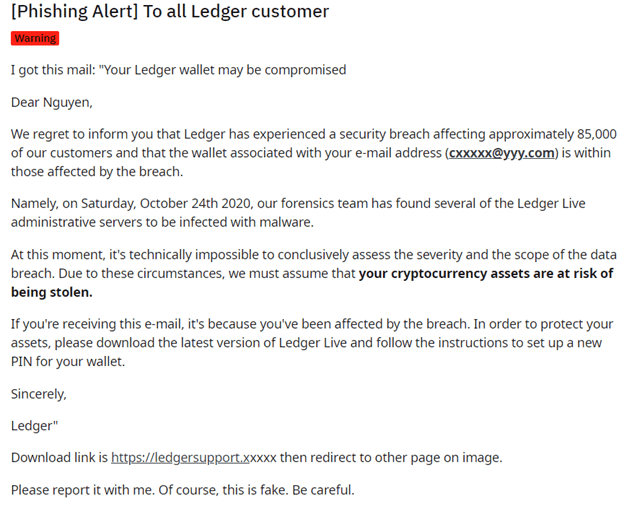
Ledger confirmed that the email looked professional and unsuspecting users of its wallet could be tempted to click. Ledger however confirmed that the email was false.
SEE ALSO: Crypto Dusting Attacks – How to Confirm Your Wallet is Affected
Recent conferences held on crypto and coin storage has revealed that even the most powerful hardware wallet isn’t invincible to attacks.
Though it seems embarrassing that some hardware manufacturers disagree with the above statement.
Ledger went further to perform some more tests, a notable test was on products from Shapeshift and Coinkite, the manufacturers of popular ColdCard Wallet.
The tests uncovered vulnerabilities that have now been fixed. The simulated attacks still required that the hacker must have physical access to the device to access its PINs.
Physical access remains a critical factor to compromise of these devices and as such, devices must be kept carefully.
Ledger submits that hardware wallets are still the safest place to store Bitcoin and Altcoins. And it is still worth holding cold wallets by all standards.
In this post, we will take a closer look at the hardware wallets and its vulnerability to hackers.
The possibilities of hardware wallets being hacked, reasons Bitcoin holders need hardware wallets, and if there are other wallet alternatives.
Let’s start with the basics.
What are Hardware Wallets?
A hardware wallet is physical USB-like device for storing cryptocurrencies offline, they are also referred to as cold wallets.
To compare characteristics of cold wallets from hot wallets, see this post.
Hardware wallets remain one of the safest places to store your cryptocurrency. With your private keys, backup, and multi-signature abilities, hardware wallets give the best coin protection.
Trezor model wallets and Ledger wallets incredibly now have multi-signature abilities.
Multi-signature wallets provide an added layer of security, one or more cosigners can be added to sign and complete a transaction. The multisig wallet uses the Pay to Script Hash (P2SH) advance mode of Bitcoin which allows a sender to commit funds to a hash or an arbitrary valid script.
The multisig technology uses the n-of-m signature config where all signatures must approve before a transaction can be completed.
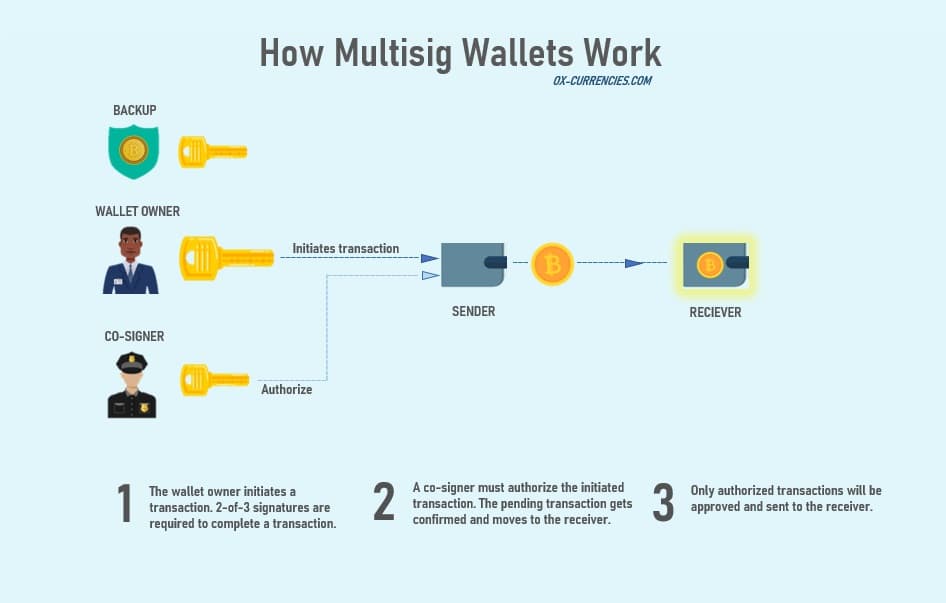
Hardware wallet users can now enjoy better security and peace of mind with the multi-signature features.
See best hardware wallets with multi-signature compatibilities.
What Extra Does Hardware Wallets Offer?
Unlike their online or soft wallets, the hardware wallets simply act as a strong vault that has a slot that users can use for transactions.
Every transaction a user wishes to carry out would have to be done through a small slot. And so, through this, the hardware remains concealed.
The hardware wallet has an additional security system – a PIN code. For maximum security reasons, your hardware wallet should be backed up. This is due to destruction, theft, or loss.
The hardware would require users to store a seed phrase. The seed phrase is a list of words that allows users access to their cryptos on a new hardware wallet.

How Can a Hardware Wallet Truly Get Hacked?
Hacking a hardware wallet is as simple as getting your private keys – that is essentially what every attacker needs to get access to your cryptos – your private keys.
A hardware wallet can also be hacked if…
1. The attacker replaces the firmware of the hardware wallet, or simply replicate the secure elements of the wallet with a bad chip.
2. Another way is to install hardware implants to carry out malicious USB attacks.
Any of the above methods would retrieve your private keys and give the attackers free access to your cryptos.
What are the Limitations of hardware Wallets?
While the hardware wallet comes with a lot of advantages, there’s no denying that there are some limitations that hinders the efficient use of the device.
1. The first limitation of the hardware wallet would be the inconvenience in usage. Unlike its software wallets that can be accessed from a mobile device. Having to carry or hold a hardware wallet could get cumbersome and subsequently hard to operate.
2.The hardware is also not fully foolproof. For instance, a physical attack on the user and threat from the attacker would compel the user to yield and release its security features.
One more limitation is…
3. It’s still vulnerable to hacks through dusting or what is known as dusting attack. How it works is that an attacker sends tiny, un-spendable number of coins or token known as dust to a pool of wallets running in hundreds of thousands.
Dusting attack is difficult to detect unless you know how to spot it.
SEE ALSO: Crypto Dusting Attacks and Clever Ways to Prevent it
Which is Safer to Store Cryptocurrency, A USB Drive or a Hardware Wallet?
This is usually a frequently asked question…
Users might often get confused as to what device is safer for storing their cryptos.
Well, I’ll will try to explain this.
First, you must know that the Hardware wallet was specially created for storing and transacting your cryptos. That is, it comes with a lot of security setup to keep your funds safe.
For you to complete a payment transaction with your hardware wallet, it has to get signed or approved with your private key.
This, therefore, give you total control of your funds. Without this private key, other users won’t be able to use your wallet. The process becomes safer as you won’t have to physically type in these private keys before carrying out a transaction.
All you need do is simply press a button and you’d get on with your transaction.
And if your wallet happens to get stolen, lost, or damaged, you need not worry about losing your funds, you can still access them through a Seed phrase.
Lastly, the hardware comes with a PIN code that automatically resets itself if your key has been imputed wrongly several times.
This only means your funds are secured and safe even when lost, stolen, or damaged.
Now let look at USB Drives (memory stick).
USB drives were not created for cryptos but can store cryptocurrencies.
USB drives are encryptable and thus provides extra layer of security.
There are several other uses of the USB Drives. The USB Drive can be used to send files, store files and act as a recovery device to your PC.
It does quite a lot and so it’s not specifically created for cryptos.
A USB Drive cannot sign a transaction unlike the hardware wallet that can transact and store at the same time.
The USB Drive is best used as a cold storage system for cryptos instead of transactions.
If you have nowhere to store your crypto currently, then the USB drive should get the job done for you.
Simply save your private key on the drive and store it away in a safe place, your funds should be safe.
Final Thoughts
The hardware wallet is a much more secure and better place to store your cryptocurrencies.
The hardware wallet is certainly not a guaranteed safe place to store your cryptos but if you want something near perfect, then a hardware wallet is your best option.
Image credit: Website vector created by stories – www.freepik.com
Read More