When Satoshi Nakamoto completed his first Bitcoin transaction of 50 BTC in 2009, he possibly didn’t anticipate that the confidentiality of cryptocurrency transactions will in a few years become a getaway bill for criminals to fund their trades through the use of the Bitcoin.

With the surge in Bitcoin related crimes since 2013, the public began to poke the safety of the cryptocurrency in the first place.
Being unregulated by government and its perceived advantages of being a very flexible payment network, the safety of the peer-to-peer payment system via Bitcoin was becoming a problem.
Hackers vanished with huge sums of Bitcoins without a trace, wreaking havoc to an originally regulated financial system.
The use of Bitcoin for instance fueled many cyberattacks through ransomware.
SEE ALSO: Crypto Dusting Attacks – How to Confirm Your Wallet is Affected
SEE ALSO: How to Flee these 10 Bitcoin Scams Now!
Foiling WannaCry Cyberattack
In May 2017, a global spanning ransomware codenamed – WannaCry attacked over 200,000 computers in over 150 countries.
Hospitals in the UK had a large number of their systems shutdown as the hacker posted ransom figures on individual computer screens, demanding payment with threats of a nationwide lockdown.
Thanks to MalwareTech who arrested the situation and made sure the attack didn’t progress beyond its infant stage.
Analysts predicted that it could have been worse with a threat of a second phase of the cyberattack that eventually was nipped in the bud.
The attention of government was drawn to the fierceness of these nefarious act as national secrets and treasures were prone to future cyberattacks.
Asides the police making frantic efforts to foil cryptocurrency crimes, cryptocurrency owners needed to do more to protect themselves and their digital assets.
SEE ALSO: Cryptojacking Attacks – Clever Ways to Detect and Prevent it
Bitcoin’s Public Ledger – Blockchain Analysis
It’s a new dawn, cryptocurrency thieves who still think that the privacy of the blockchain network still enables them have a fill day are really making a big mistake.
Without a doubt, Bitcoin has many legitimate uses.
Many other altcoins like Ethereum and Ripple are benchmarking Bitcoin’s dominating features and offering some extras in terms of mining speed and flexibility.
Unlike the Fiat currencies which presents a variety of measures to crackdown money thieves, the police now have a strong tool to crackdown cryptocurrency criminals.
You now stand a chance of tracking a cryptocurrency criminal who might have stolen from you in the past, the police now have access to the public ledger known as the blockchain and are mastering how to investigate cryptocurrency related crimes.
With this new development, they have recorded series of arrests using the public ledger in cracking down criminals.
Follow the Crime not the Means
A 23-year-old South Korean man was accused of running a the “largest child sex exploitation market” and successfully completed 7300 Bitcoin transactions worth $730,000.
The owner of the website, Jong Woo Son named his website “Welcome to Video”. It was reported that over 250,000 child sex exploitation materials with an enormous file size of about 8 terabytes of immoral content was seized from him at the time of his arrest.
“Welcome to video” was launched in June 2015 and was closed down by the U.S. authorities in March 2018 after convicting him. Jong Woo Son was sentenced to 18 months in prison to serve in his native home, South Korea.
Here is the case file.
Fulfilling payment was Bitcoin’s original purpose, but its decentralized network makes it attractive to criminals.
Illegal arms dealing, drugs, human trafficking and child pornography are funded in dollars through Bitcoin’s anonymity.
The police now have the lead, they know that these class of high-powered criminals are most often linked to the cryptocurrency blockchain network.
Dark Websites and the Darknet
Dark web sites exist only on darknets, which require special system configuration or software to access.
Basically, dark web is that area of Internet that every day user cannot reach.
The only way to access it is through special network of browsers such as TOR which stands for The Onion Router or maybe I2P. Special VPNs can also be used to gain access to those sites.
Dark web has those sites which you cannot reach by mere typing in a URL, in fact if you do not know their originating source. Chances are, you will never find them even through TOR.
These dark sites look much like a regular webpages or websites we visit every day, but note that they are not the same.
One way to differentiate them is by their weird domain extension.
Instead of the seeing the regular .com, .net, .org, you should see. onion. It is a special level domain that can only be accessed via the TOR.
For example, a dark website could have domains like “fxxpiyy29jsg.onion” or ppgggxx4dhh.onion. These domains are crafted this way for a purpose – They want to stay anonymous, making them very hard to memorize of pronounce.
How Dark Websites Relate to Cryptocurrencies
Dark websites are setup by scammers, hackers and all sorts.
They do this to avoid being traced by their victims, it’s an underworld for online criminals.
With these dark websites, they stay masked and hidden. Dark websites are responsible for trojans and all forms of malware injections into legit sites.
Hackers do this for many reasons, the least which is to redirect web visitors to another webpage, the most gruesome which is to press for ransom or blackmail a web user.
Dark websites trade illegal stuff, nothing legitimate originates from their servers.
Illicit trades not needing human intervention thrive and most times get funded via cryptocurrencies mainly Bitcoin.
Silk Road or Valhalla traded illicit commodities in the past. Both of these websites were taken down by law enforcement few years back.
The police should then know that there are dedicated dark web search engines to access the darknet. For instance, the Hidden Wiki, DuckDuckGo, Candle, SearX and some others dark web search engines are gateways to these websites.
Dark websites do not host websites like Google, but it is still possible to navigate the dark web with the above listed search engines and directories.
This is why dark web is considered a wild park and a dungeon of the internet. Dark websites must be accessed with caution and with expert knowledge.
Where the Police Should Look
When Bitcoin was first introduced, it seemed it was only for a select class of high net worth stocks and forex investors.
It took government agencies some time to get a hold on the whole cryptocurrency system and its technology. Unfortunately, the surge in price of the Bitcoin renewed interest of the public who now exchanged Fiat currency for Bitcoin just to benefit from its capital appreciation.
For the first time since in October 12, 2009, Bitcoin raced from $0.0009 to touch its highest point thus far at $20,089 in December 18, 2017.
The boom initiated a new wave of Bitcoin owners and traders exchanging the 21,000,000 BTC already in circulation. About 88% of these coins has already been mined.
This now narrows the scope to about 12% within the police radar which they can track through the following means:
SEE ALSO: Beginners – How to Earn Bitcoin Without Buying It.
Cryptocurrency Receipts
This is relatively new especially with the introduction of cryptocurrency automated teller machines ATM.
Receipting is vital to a successful tracking of peer-to-peer transactions.
If the police are going to crackdown cryptocurrency related crimes like money laundering and funding of terrorism, it must stay ahead of criminals.
Recently, Bitcoin, Litecoin, and Ethereum are available on selected ATMs.
To track cryptocurrency theft, the police department scrutinizes transaction receipts on the ATM with public blockchain ledger to help investigate.
Another way around this is for law enforcement agencies to flip ATM owners and recruit them to assist.
Mining Equipment

With mining hardware been an evident infrastructure for cryptocurrency dealings, the government through the police can perform security checks on computer mining hardware.
Most cryptocurrency mining equipment are identical. Either there are many CPUs linked together in a datacenter or multiple rectangle boxes with fans attached to them.
If the computing hardware does not look like your regular computer then chances are it might belong to miner.
SEE ALSO: Crypto Dusting Attacks and Clever Ways to Prevent It
Digital Wallets
Digital wallets differ from a regular back-pocket wallet.
Digital wallets make use of two type of keys, the public and private keys.
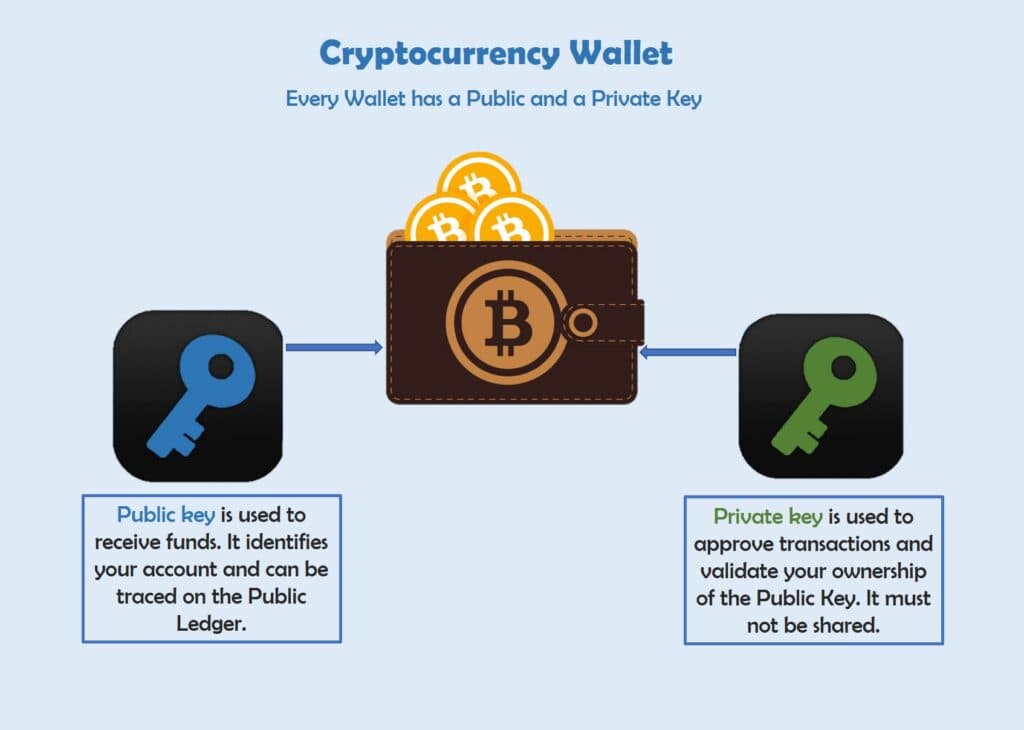
With many cryptocurrency digital wallets now available to users, the web-based version requires internet connection to access them. The hardware wallets are offline and relatively safer.
The police should not bang on doors requesting for declaration of digital wallets, either web-based or offline hardware wallets.
The police should however know what to look for when examining a cryptocurrency wallet.

Taking little steps and recognizing and documenting cryptocurrency elements will help the police to largely minimize the spread of these crimes all over the world.
Kathryn who led the case for the infamous Silk Road case revealed that they were able to crackdown the men behind it despite it being a cryptocurrency transaction.
The Europol cybercrime analyst BTC makes paper trail which can accelerate cryptocurrency trails and detection. Unfortunately, some cyber-criminals still think they are invisible.
Even if hackers use stolen algorithms and injection schemes to gain entry into a victim’s system, their configurations don’t spare them of bugs that leave an evidence behind.
So, Law enforcement can use their tactics and get blockchain analyst to securitize and trace proceeds of crime.
What the Police and Law enforcements Must Do
Juniper Research in one of its publications stated that, by year 2022, cyberattacks will cause around $8 trillion damage to the global economy.
Cyber security Ventures predicted that ransomware might attack around every 11 second compare it with every 14 second back in 2019.
The law enforcement should come up with workable measures to counter these attacks. If too late, it might get out of hand in future.
Ultimately, the government needs to regulate the cryptocurrency with altering its decentralization model. This should make the use of cryptocurrencies safe and restore its compromised blockchain infrastructure.
Read More