Ever thought how possible an illegal miner would steal from the proceeds of a legit mining activity without the miner knowing?
If you thought this was not possible, then think again…
Cryptojacking is just one way of stealing a miner’s computing power and reward through the use of some malicious program.
In 2018, researchers found that a new Monero cryptojacking malware “Crackonosh” got widespread through video games, wiping out antivirus programs on computer systems and secretly mining cryptocurrencies in dozens of countries.
The dubbed malware hibernated on cracked versions of best-selling video games…Grand Theft Auto V, Pro Evolution Soccer 2018 & NBA 2019. These cracked versions distributed this malware like wildfire.
Gamers could download these pirated versions for free on game forums or some other game sites online.
Commercially cracked games were free but came with a benefit exclusively to the fellow that cracked it.
Gaming is just one of several ways cryptojacking infiltrates peoples’ systems, devices, and lives.
Overall, Crackonosh malware mined over $2 million of Monero from 222,000 hacked computers, Hackernews reported.
One would wonder about the link between video gaming and crypto mining.
What then should cryptocurrency miners and enthusiasts know about cryptojacking?
Cryptojacking is a subtle way cybercriminals hack into unsuspecting victims’ computers to steal computing power and mine cryptocurrencies without the users hardly noticing.
Computing mining resources of the unsuspecting victims are stolen while their wallets hardly ever getting the commensurate value of what was mined.
Let’s see some stats on cryptojacking at a glance.
Quick Facts about Cryptojacking
• Cryptojacking activities surged and got to its peak in 2017 with more than 8 million cryptojacking events blocked by Symantec.
• Over 25% of businesses have been victims of cryptojacking.
• Over 25% of WordPress plugins in notable websites were flagged with vulnerabilities that exposed them to mining botnets.
• Systems infected with cryptojacking scripts have tendencies of loading 5-7 minutes slower than expected.
Before sharing how Cryptojacking works and how to prevent it, let’s first understand this weird crypto term which is now used to communicate this type of horrendous cybercrime.
What is Cryptojacking?
Cryptojacking is a type of cyberattack where an attacker gains access to a user’s mining device, through malicious software and uses its mining resources to mine cryptocurrency.
Cryptojacking attacks extend beyond individual systems, it can be launched on small and larger corporations. Mobile devices, large CPUs, and GPUs are no exemptions to Cryptojacking.
Imagine a bank teller transferring $0.01 from the account of 1000 depositors in a commercial bank. Say he connives with the IT staff to run codes that could do these deductions and transfer from the depositors’ accounts to a dummy account of his for the next 30 days, this amounts to $300.
Assuming he extends this attack to 100, 000 depositors, that amounts to $30,000 in 30 days.
This could happen and victims would not suspect these tiny deductions from their balances for a long time.
In 2018, a Spanish company Panda Security foiled an attack on a malicious Cryptojacking script used to mine Monero also.
The attack was nicknamed “WannaMine”, this script was launched across computers silently infecting their systems with an algorithm known as “CryptoNight”.
CrytoNight ran an algorithm on infected systems over and over to guess hashing requirements much faster than the user’s legit software’s algorithm could solve.
Below is an example of a crypt0jacking script from CoinHive botnet, it infiltrated its min.js file on the livehelpnow.net website, a messaging and voice call business.
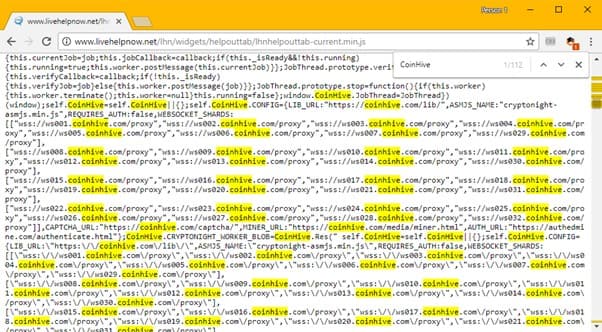
This goes to show that other online businesses asides from crypto are not spared.
Methods of Cryptojacking
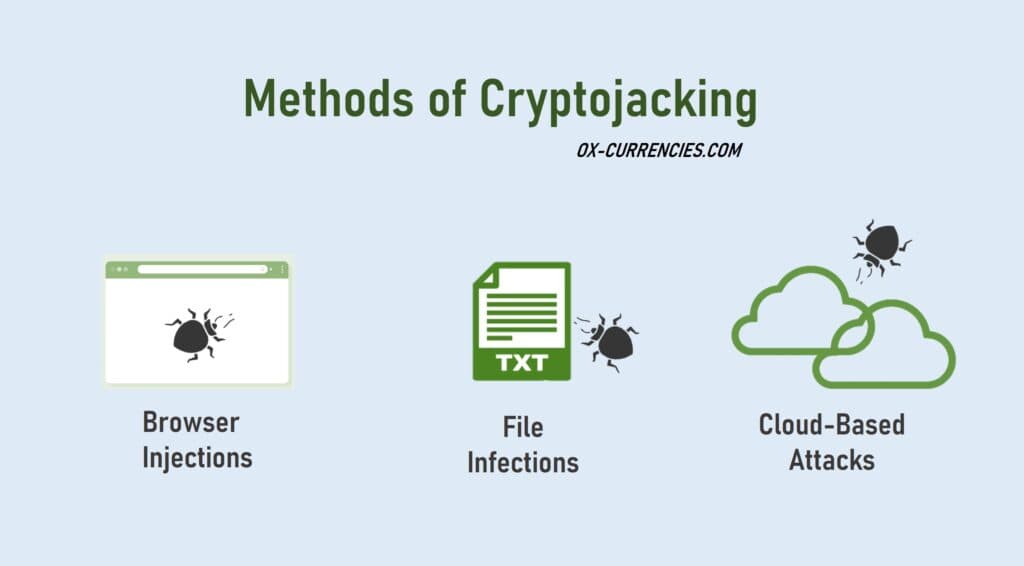
There are 3 identified methods of cryptojacking. It can also be referred to as cryptojacking gateways or access points.
• Browser injections
• File infections
• Cloud-based.
Cryptojacking attacks occur through these 3 channels.
Let’s then examine how cryptojacking works.
How Does Cryptojacking work?
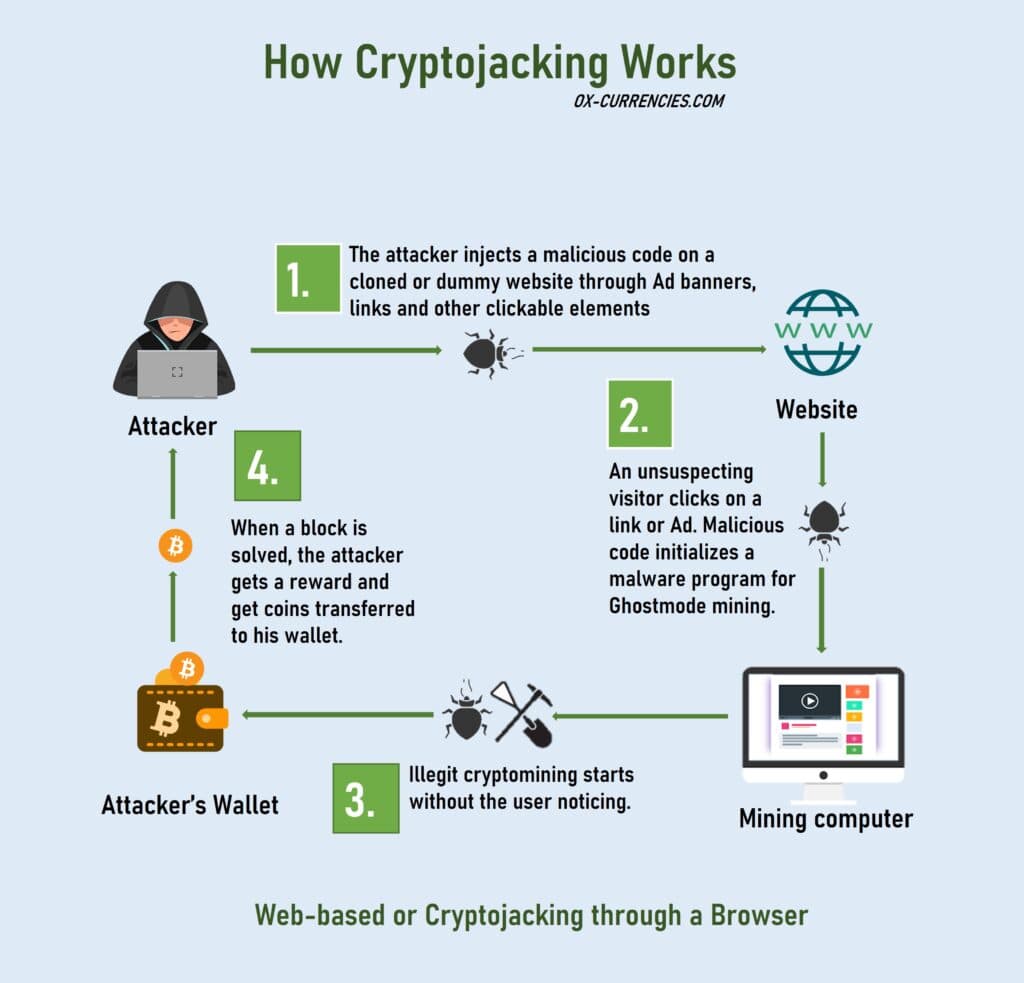
There are four basic parts to the cryptojacking puzzle, but I will explain how it works.
Step 1. An attacker launches a widespread malware attack on dozens or hundreds of cloned or dummy websites.
Again, legit websites with no or weak firewalls and antispam blockers could also be infected.
Note that target websites are usually crypto-related attracting lots of cryptocurrency enthusiasts. Crypto news sites, gambling, casinos, betting, staking sites are prime targets.
Step 2. Web visitors land on these websites and click on an element
(banners or links), a cryptojacking script is injected, downloaded, or installed on the visitor’s system without him/her knowing.
When the script is successfully injected, the algorithm initializes and does its first set of installations on the system preparing for the next mining activity.
Asides from websites, email phishing is another channel. See the image below revealing details of what a typical cryptojacking email looks like.
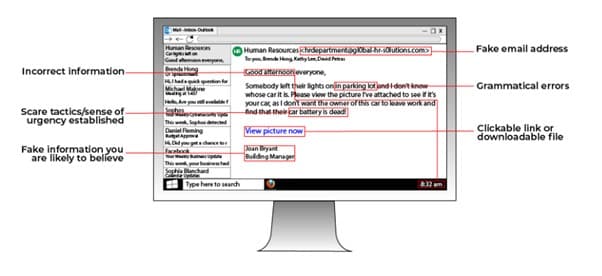
Step 3. When mining resumes, the cryptojacking script block or limits the legit software from hashing blocks efficiently (depending on how the malware was programmed).
The user may notice a decreased performance in his mining software and possibly overheating. He may not be able to ascertain what went wrong.
Step 4. When a block is solved, the attacker gets rewarded for the cryptocurrency illegally mined.
The user may notice a decline in expected revenue but may not be able to figure out the cause.
The volatility of cryptocurrencies may also make it difficult to monitor block reward expectations.
Since the crypto-mining malware is the culprit illegally doing the mining work, let’s examine the most notorious cryptojacking malware.
Examples of Cryptojacking Malware
Cryptojacking malware when compared to ransomware was seen as less threatening because money didn’t change hands, however, companies needed to remove these systems bleeding botnets out of their systems.
In 2019, 8.9 million websites were found to be hosting these cryptojacking scripts.
21stcentech noted that this malware could creep into systems without the HyperText Transfer Protocol (HTTPS).
In the same year, Webnotes in a report stated that 7.8% of businesses had cryptojacking infections while 12.6% of home systems were ladened with such infections.
Upon analyzing the cause of these cryptojacking activities, botnets and ransomware were major culprits.
A few of these are cryptojacking malware are…
Dridex – This was a prominent botnet banking trojan.
Retadup – This malware hijacks the host and limits crypto mining efficiency. It causes serious diminishing performance of the system, attacking mainly Windows-based systems.
HiddenBee – This botnet trojan injects heavy payloads on unsuspecting systems through image files such as WAV Flashplayer media, GIFs, JPEG, and PNGs. It burdens the system and mines secretly.
Other cryptojacking malware includes Cryptoloot, Coinhive, REvil, TrickBot, CoinImp, CrySIS.
How to Detect Cryptojacking
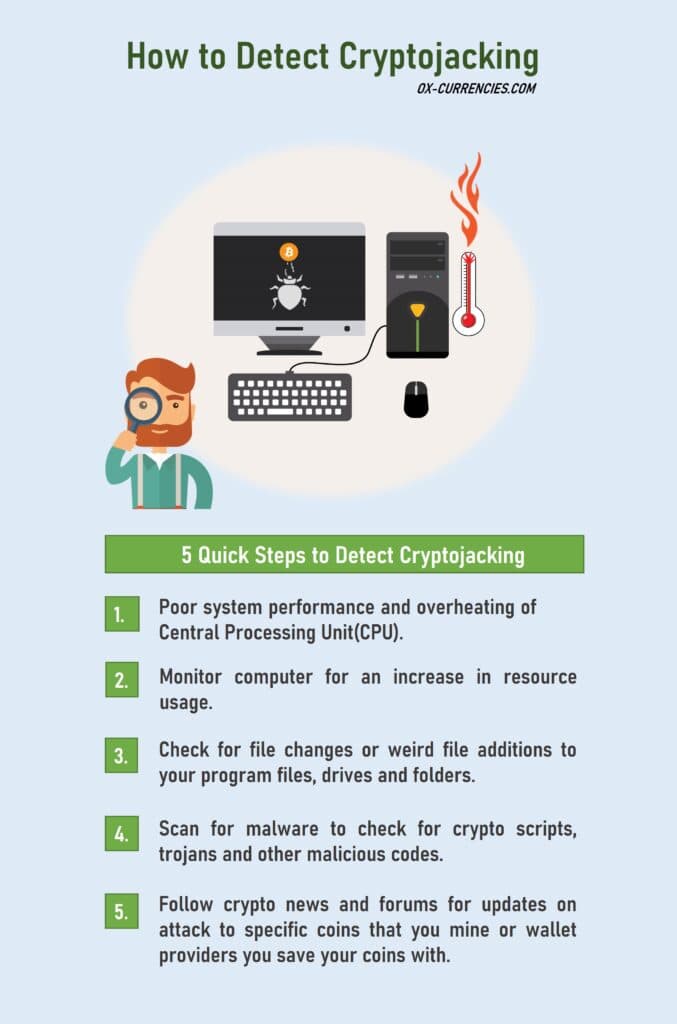
Detecting cryptojacking can be somewhat challenging if don’t know what to look out for.
But they’re just a few ways to detect the presence of cryptojacking botnets running in a computer’s system background.
What draws the attention of an unsuspecting miner is the quick usage of computing resources which slows down the system.
Despite powerful mining processors and software, the presence of cryptojacking malware doubles the use of computing resources which adds extra loading time and slack.
Increased usage of computing resources means more power is required. More power then increases the heat generated on the device.
A slow system requiring more resources is accompanied by overheating of the CPU.
A third way to detect cryptojacking is the addition of strange files.
You may notice some modifications or additions on your doc. js or txt files.
You should check for the file creation date, if it’s very recent, isolate and scrutinize the files, it could have been just created for malware attacks.
The challenge is that this approach can be very tedious for detecting malicious files especially when you have hundreds of them.
It’s recommended you use an antimalware scanner to run a quick scan.
With a scanner, the presence of malware will reflect on its report with links pointing to the hidden spots so you can easily find them.
How to Remove Cryptojacking Malware
To remove cryptojacking malware, you need to establish the type of devices that were infected as all have a different approach…
Malware Removal Tools for Desktops
Norton Antivirus
First, run your device through scanners like Norton Antivirus.
Norton runs a comprehensive system check through its machine learning technology for bad files.
It also does routine system checks to block trojans on the device.
Norton automatically isolates suspicious files and trashes them. You can use the free trial version to get basic scans done on your device.
There are other notable cryptojacking malware blockers for Windows PC…
- BitDefender
- Avira
- BullGuard
- Kaspersky
- Eset
Malware Removal Tools for Websites
Sucuri
For websites Sucuri is a brilliant malware scanner, many hosting companies recommend Sucuri. This app scans for infected web pages and sends a report.
The report tells if your website has minimal or critical security risks and guides how to fix them.
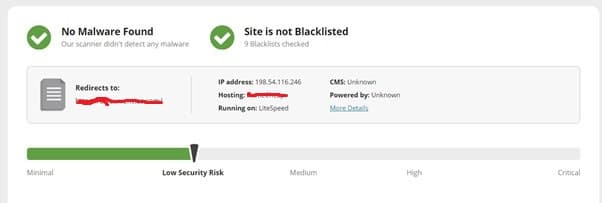
If you know how to spot malicious codes, you can use its report to DIY. Secondly, pay a sum of $199 for Sucuri’s professional malware clean-up service.
MalCure Web Security
Another cryptojacking malware remover to use is MalCure Web Security.
The MalCure hunts down malware and uses its powerful scanners to lead the user to malware spots.
Clever Ways to Prevent Cryptojacking
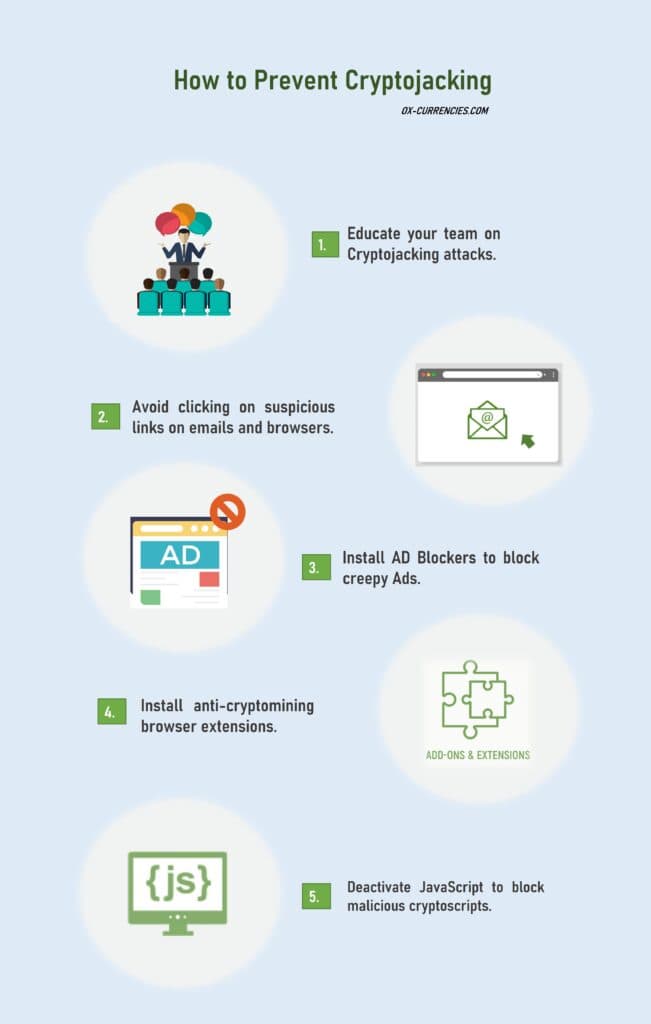
It costs a lot less to prevent cryptojacking attacks than it takes to remove an already-infected device.
First, staying up to date with cybersecurity tips and guidelines goes a long way to keep you and your team alert to these dangers and inconveniences.
Training and constant sensitization with your team are oftentimes overlooked but it saves everyone headaches down the road.
To prevent cryptojacking attacks or any other associated crypto mining scams. It’s best to observe the following.
• Training and education of your team.
• Installation of cryptojacking malware blockers.
• Set parameters to send suspicious email addresses and spam links.
• Install firewalls and spam detectors.
• Remove unwanted JavaScript codes (with the help of an expert).
• Perform routine scans to spot passive trojans and botnets.
• Change security login details frequently.
• Tighten security with 2-factor authentication.
Final Thoughts
Cryptojacking may seem like a relatively crypto terminology, but it has been there all along.
Taking precautions is always less expensive than fixing when issues arise.
Stay alert and look out for all your digital assets by protecting a system free from malware.
Store your assets in digital wallets that are safe and secure, visit this post 5 Best Bitcoin Wallet Providers in 2021
Image credit: Design vector created by pikisuperstar – www.freepik.com
Read More