Cryptography consisting of public keys and private keys has always been of maximum importance to cryptocurrencies; without it, no transactions are safe, and no information’s integrity is maintained.

Key Takeaways
•Hashing is done primarily to reduce the hazards of easy decryption. When the conversion is complete, the stored value relates to the digital fingerprint or hash value.
•Public key cryptography is used in a wide variety of protocols and data formats that are supported by a wide range of applications and system software. SSL, SSH, digitally signed PDF files, OpenPGP, S/MIME, and other protocols are examples.
•The public key is used for encryption, but only a private key may be used to decode the data. That being said, it is feasible to obtain a public key if you have a private key, but it is very difficult to obtain a private key using a public key.
Consider this: when you do peer-to-peer (P2P) transfers, your data may be exposed in the absence of safe encryption, and anybody might attempt to read the data structure without knowing the data has been tampered with.
That is why private and public keys are so important in authorizing these transactions.
While both the public and private keys attempt to safeguard a transaction, they are noticeably different in order to serve their respective functions.
A public key is used to validate a transaction after a transaction has been requested when comparing them side by side. A public key is sometimes interpreted as a ‘address’ for receiving cryptocurrency.
A private key connected with a bitcoin account, on the other hand, concentrates on transaction authorization.
A private key is typically not shared, and only the owner should have access to it. In other words, anyone with access to your private key will be able to deplete your wallet assets.
That is why you must comprehend what they are and why they are so vital. Perhaps to learn how to avoid becoming the person who has locked up millions of dollars in Bitcoin holdings.
What is a Public and Private Key
A public and private key are used to decipher communications that have been encrypted using a complicated mathematical process inside the cryptography approach.
While a public key can be publicly circulated, a private key used in cryptography is designed to be held secretly as a password to protect your crypto assets.
Typically, these private keys vary based on the type of cryptocurrency, although practically all of them utilize 256-bit encryption. This contains BTC, ETH, LTC, and other cryptocurrencies.
For example, a Bitcoin private key is given below:
0x01 and 0xFFFF FFFF FFFF FFFF FFFF FFFF FFFF FFFE BAAE DCE6 AF48 A03B BFD2 5E8C D036 4140, representing nearly the entire range of 2256-1 values.
An example of a public key is given below:
3048 0241 00C9 18FA CF8D EB2D EFD5 FD37 89B9 E069 EA97 FC20 5E35 F577 EE31 C4FB C6E4 4811 7D86 BC8F BAFA 362F 922B F01B 2F40 C744 2654 C0DD 2881 D673 CA2B 4003 C266 E2CD CB02 0301 0001.
The key is a series of random symbols that may be accessed by anybody (public key) or known only to the owner (private key) (private key).
The public key is used for encryption, but only a private key may be used to decode the data. That being said, it is feasible to obtain a public key if you have a private key, but it is very difficult to obtain a private key using a public key.
Cryptocurrency wallets are fantastic examples of how to use public and private keys. When it comes to wallets, a public key is a user’s address that allows other network members to send tokens to this wallet.
However, if a user wants to transmit crypto from one to another, they will require their private keys to complete the transaction.
You’ll need a password, just as you do when you log into your email. The email address serves as a fixed point for other email network users to send messages to. While a password is necessary to have complete access to the email account.
For the longest period, however, symmetric encryption was the dominant encryption method, in which every communication was encrypted and decrypted using the same algorithm (key). Nonetheless, it raises fundamental concerns regarding its security.
SEE ALSO: What is an Anti-Whale Mechanism and How to Protect Your Crypto Investment
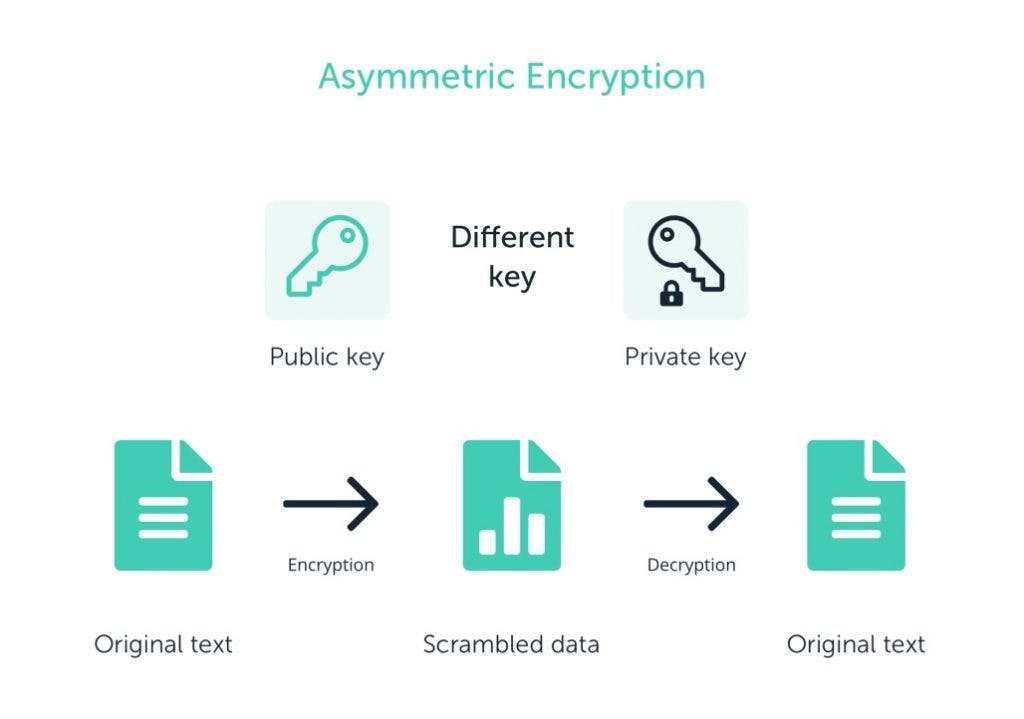
As a result, asymmetric encryption is meant to address these security concerns by employing a pair of keys (one public and one private) that are used independently to encrypt and decode communications.
In contrast to symmetric encryption, which uses a single key to encrypt and decode data, public and private keys must “match” the encrypted data. They are both created and consumed at the same time.
Cryptography Techniques Used in Cryptocurrency
There are numerous ways for cryptography in cryptocurrency, including symmetric encryption, asymmetric encryption, and hashing.
1. Hashing
Hashing is used to encrypt transactions between accounts by encoding the user’s account addresses. Random letters and numbers are added to the stored value to ensure the encryption’s security.
This is primarily to reduce the hazards of easy decryption. When the conversion is complete, the stored value relates to the digital fingerprint or hash value.
2. Symmetric Encryption
It is one of the most widely used, simple, and successful encryption methods. The communications are encrypted using a single key, which may be identical or different across parties at the same time.
It is then encrypted and sent to a receiver, where it is decrypted once received and validated.
3. Asymmetric Encryption
Unlike symmetric encryption, symmetric message encryption and decryption often include two keys—private and public keys. After a transaction has been requested, public keys are used to validate it.
A private key is used to decode the message or transaction. The idea is to keep the transaction genuine while also reducing the likelihood of a security breach. This also implies that if the private keys are misplaced, there is no way to recover them.
Similarly, if the private key is revealed, any transaction can be allowed, and it is unrecoverable because it has been authorized.
How Do Private and Public Keys Work?
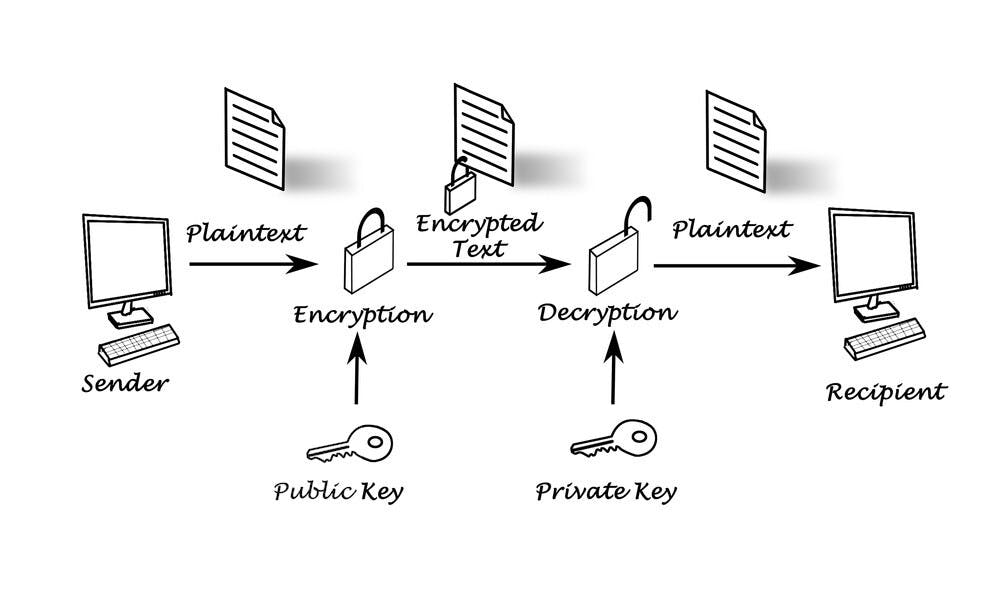
The fundamental components of public key cryptography are identity and secrecy. In basic terms, it may be stated as follows:
- The sender obtains the public key of the addressee.
- The sender encrypts data using this key.
- The sender delivers the encrypted data to the recipient.
- The addressee decrypts the data using his or her private key.
Assume Henry (sender) wishes to transmit 1 BTC to Maria (recipient). He is aware of her public key and employs it to encrypt the transaction. Maria gets the transaction and uses her private key to decode Alex’s 1 BTC transfer.
Maria should be the only one who can authorize the transaction because no one else has access to her private key.
A private key is what you physically hold when it comes to cryptocurrencies. It establishes your authority to control your crrypto assets and allow transactions. Whoever has this key can spend the crypto assets linked to it.
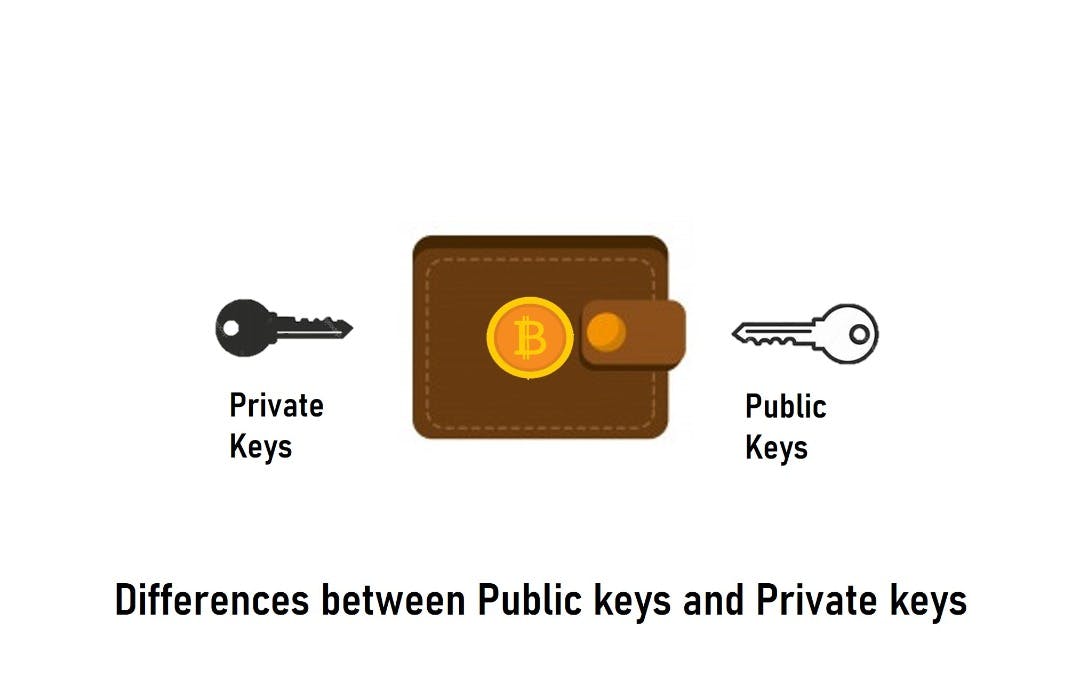
The Differences Between Public Keys and Private Keys
The purpose of both private and public keys is to ensure that a particular transaction was spent by the party who signed it and was not created out of thin air.
Though both methods of encryption serve the same function, they differ in a variety of ways. Here’s how they differ:
1. Algorithm and Mechanism
There must be two different keys for encryption and decryption in public-key encryption. The private key is solely available to the owner, but the public key is open to anybody.
In symmetric key cryptography, just one key is necessary for communication between the two parties involved.
The information is encrypted and decrypted using the same private key. It is shared by both the sender and the recipient of an encrypted message.
2. Performance
The private key mechanism is significantly quicker than the public key approach. This is because a private key only requires one key, but a public key requires two keys.
3. Privacy
The private key is kept private and is not shared with anybody other than the wallet’s owner. When the private key is lost, it is difficult to recover it, and the encrypted file becomes useless.
These keys are typically difficult to memorize due to the complicated numbering. However, the security of private keys is entirely up to the owner. That is why an offline storage device is the best way to keep your private keys safe.
The public key, on the other hand, is available to all users and should be found through a search. The public key is unlikely to be lost.
4. Digital Signature
The user’s private key may be used to digitally sign the online content, and the user’s public key can be used to verify it. This makes it simple to identify the message sender in the network and ensure that a message was delivered by a trustworthy person.
The digital signature has several security benefits, including:
- Authentication: It establishes if the message or user is lawful or not since forgery is impossible.
- Non-negation: After communication, the message sender cannot refute the signature.
- Integrity: The signature ensures that the received message has not been tampered with.
5. Encryption and Decryption
The user’s public key is used to encrypt the material, which can only be decoded with the user’s private key. That is the only method to restore the message.
Encryption offers the following security advantages:
- Privacy: There is no possibility of illegal access. Confidentiality is achieved by employing a private key known only to the owner and no one else.
- Integrity: The encryption method, which uses a secure public key, ensures that the received message is not tampered with.
Public key cryptography is used in a wide variety of protocols and data formats that are supported by a wide range of applications and system software. SSL, SSH, digitally signed PDF files, OpenPGP, S/MIME, and other protocols are examples.
It is commonly used in software applications like browsers to enable safe connections over untrusted networks. Asymmetric cryptography serves as the foundation for the blockchain algorithm, which serves as the foundation for all cryptocurrencies.
SEE ALSO: Coinkite Cold Hard Wallet Vs Ledger Nano X – Which is Better?
Frequently Asked Questions (FAQ)
1. What exactly are private keys in cryptocurrency?
A private key is an advanced type of cryptography that allows a user to access their cryptocurrency. A private key is an essential component of bitcoin and altcoins, and its security features help to protect a user’s funds from theft and unauthorized access.
2. Is the public key the same as the wallet address?
Wallet addresses are hashed copies of the public key. To make it easier to deliver an address, public keys are compressed and reduced.
Final Thoughts
Public keys and private keys are very important when it comes to cryptocurrencies. Private keys, in particular, are held in secrecy so as to protect your crypto assets. This article explains in detail what they are and lays down the differences between them.
Read More